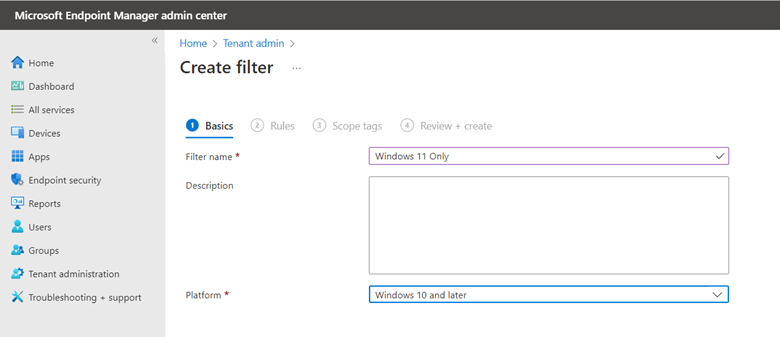
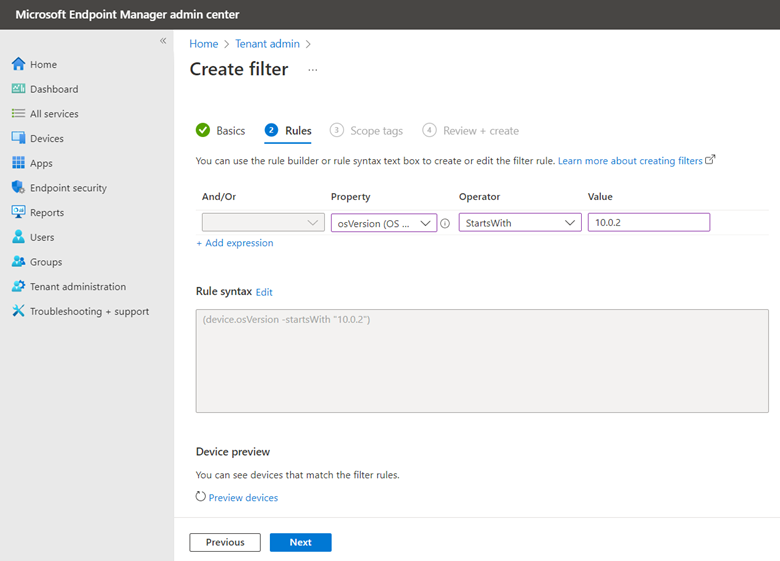
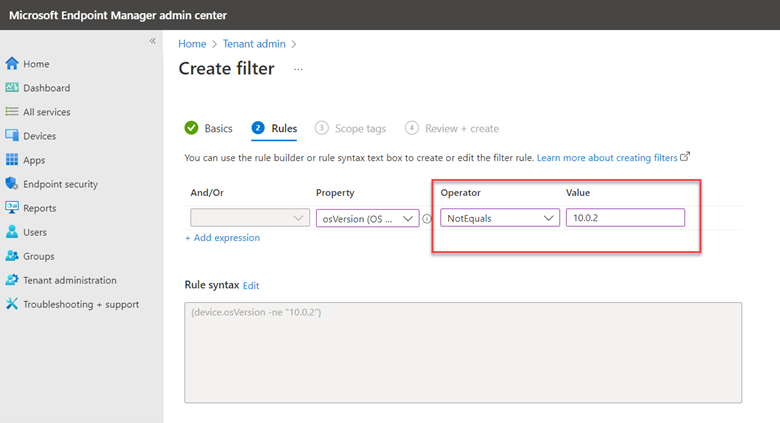
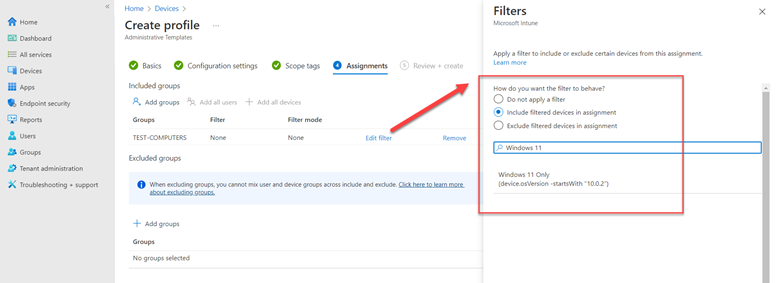
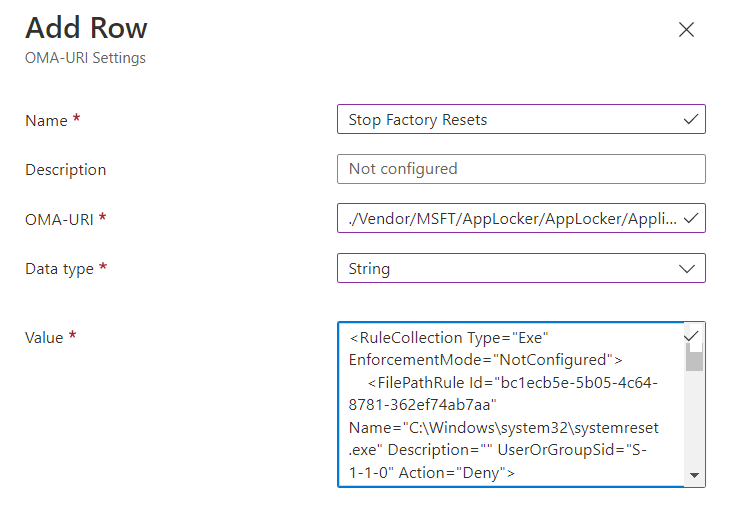
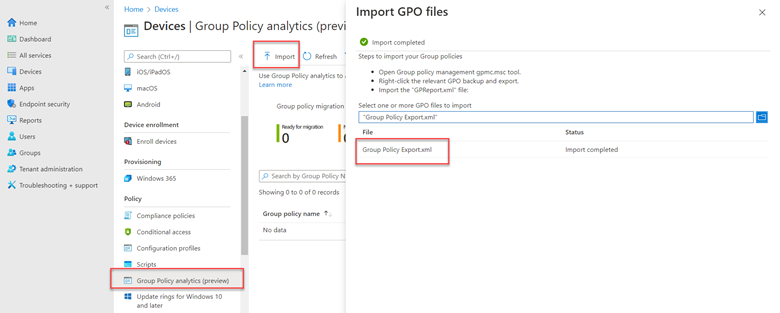
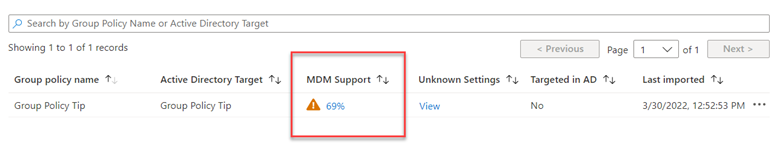
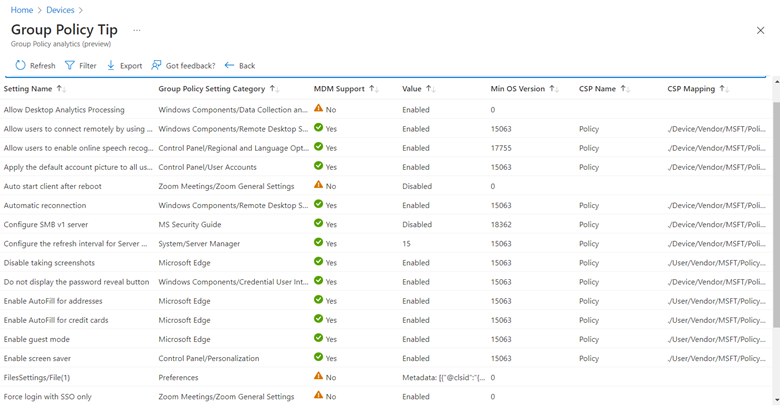
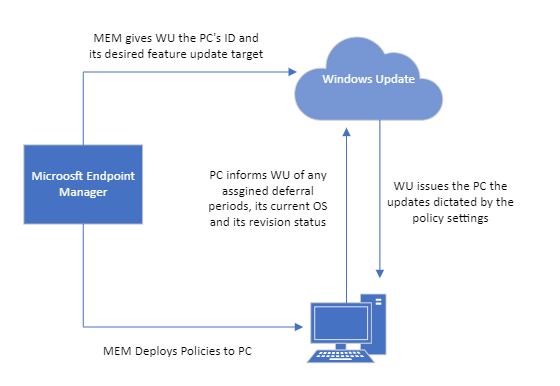
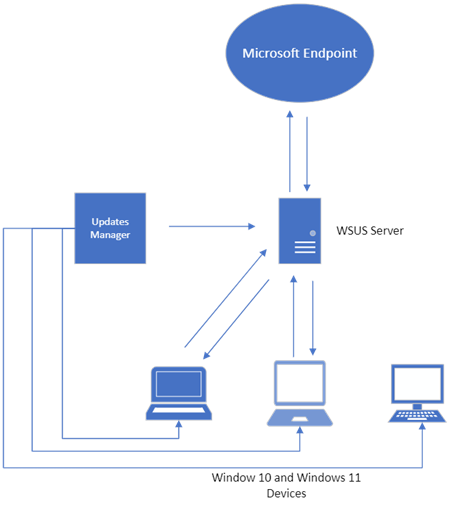
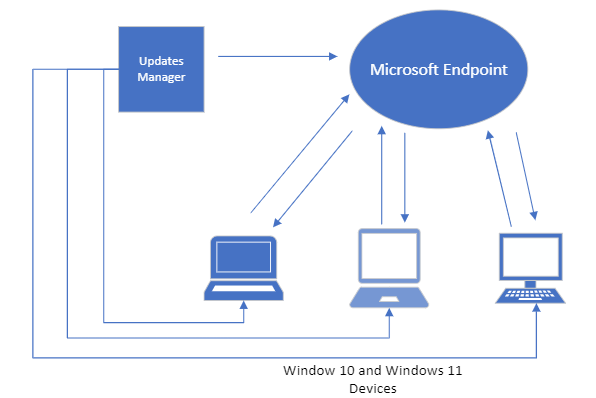
Think of WSUS as version 1.0 for managing Windows updates. Windows Update for Business can be considered version 2.0 as it is the next evolutionary step for managing updates for Windows 10 and Windows 11. Unlike WSUS, clients connect directly with Microsoft Endpoint so there is no intermediary server involved. All you need is a management tool such as Group Policy Management Console, an MDM tool such as Microsoft Endpoint Manager or a third-party management tool. The management tool is where you create the update policies and assign them to designated device groups. Once the clients receive the policy, they contact Microsoft endpoint which sends them one or more updates depending on the client’s provided inputs. If you have the Windows Update for Business Deployment service installed, the manager can talk directly with Microsoft Endpoint as well.
Deferring and Pausing Updates
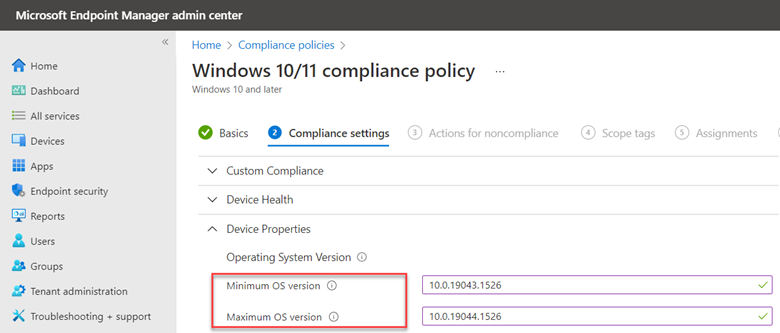
One of the enhanced features that Windows Update for Business provides is the ability to defer the installation of both feature and quality updates for a specified number of days. The deferment period depends on the type of update as shown below.
Update Category Maximum deferral period
Feature updates 365 days
Quality updates 30 days
Non-deferrable 0 days
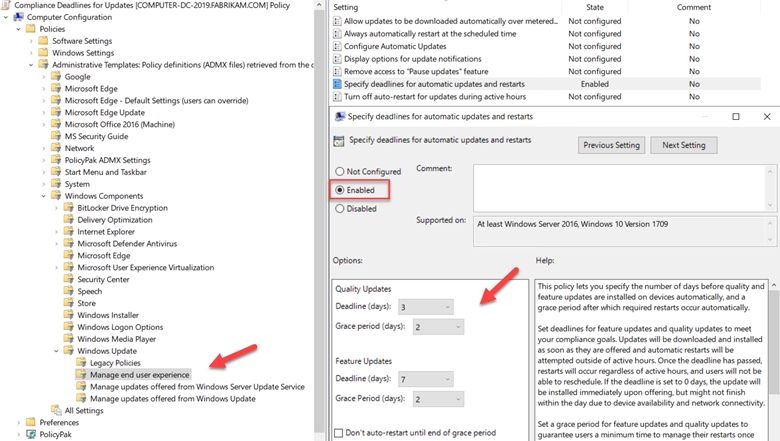
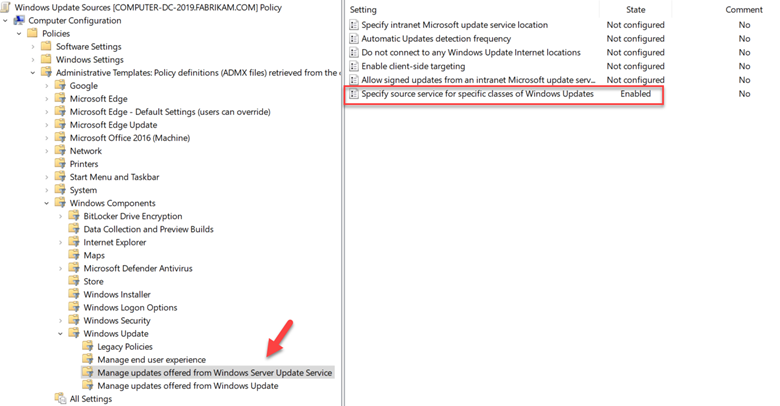
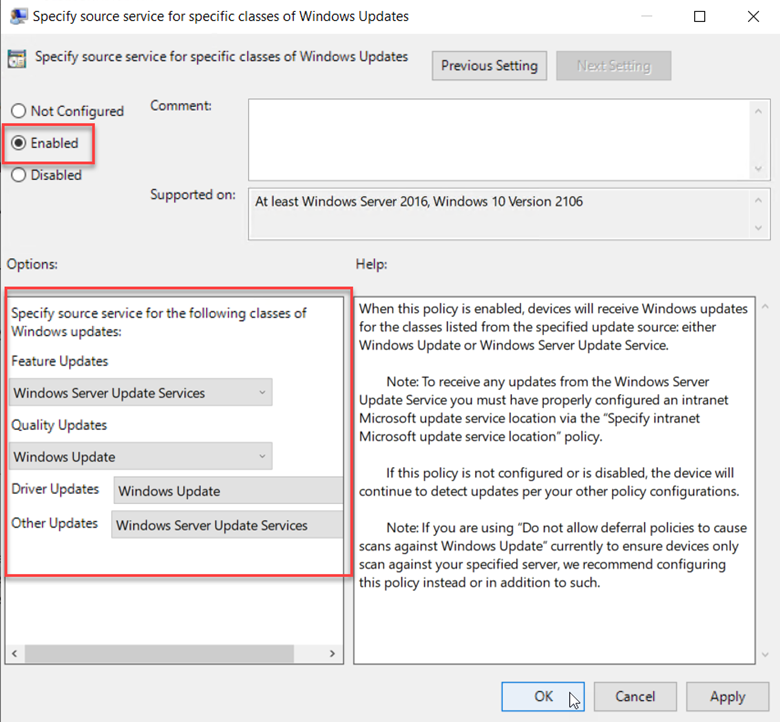
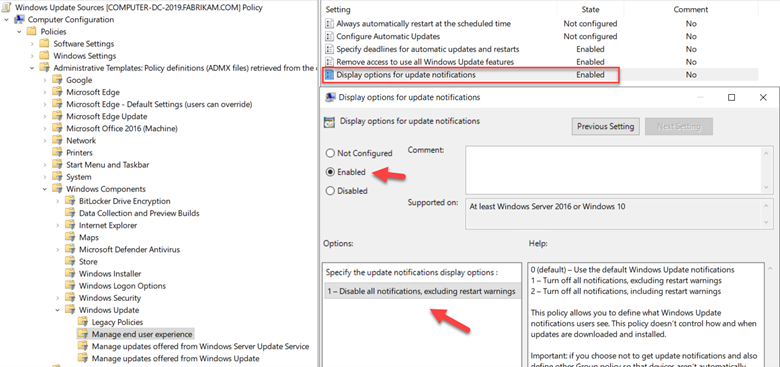
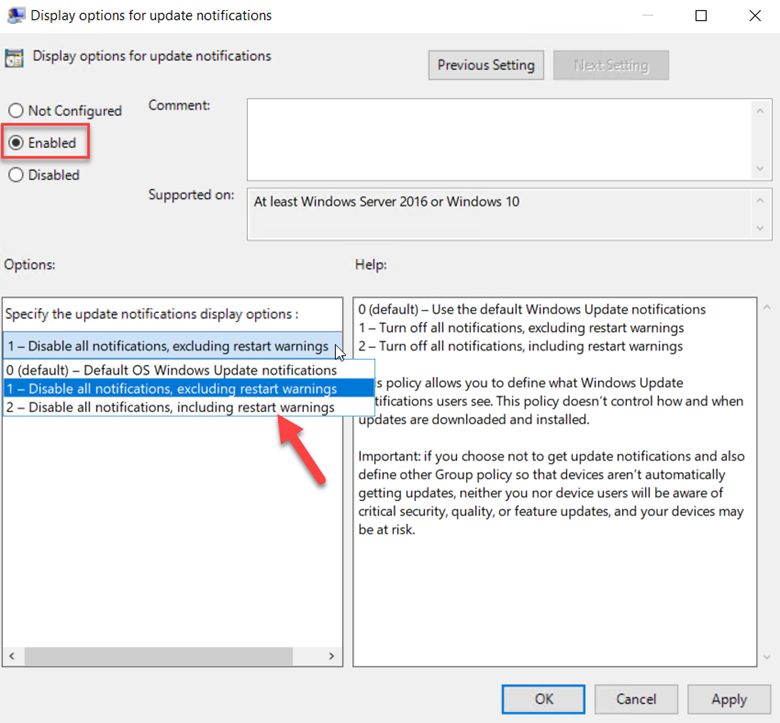
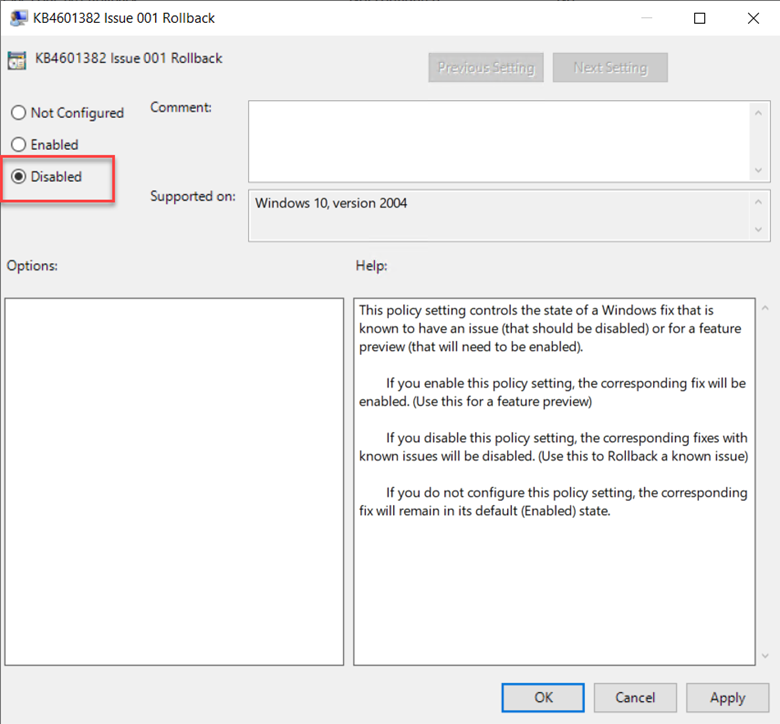
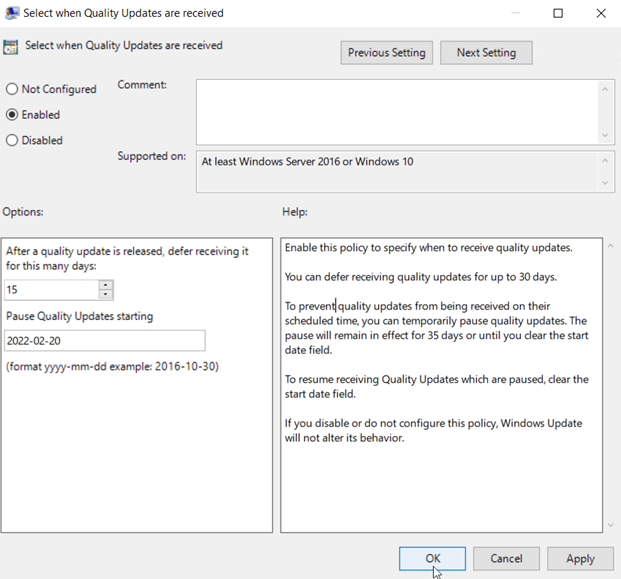
You can also choose to pause quality or feature updates all together. This is similar to deferring an update except you specify an exact date. Beginning on that date, updates are paused for 35 days. This is useful if you discover that one of the recent updates is causing problems and you want to buy some time to conduct further testing. You can configure the required settings to defer or pause an update using Group Policy. Create a GPO and go to Computer Configuration > Administrative Templates > Windows Components > Windows Update > Windows Update for Business where you will see several policy options. In the screenshot below, we have configured a deferment period of 15 days as well as a specific date to start pausing Quality updates.
Windows Update Rings
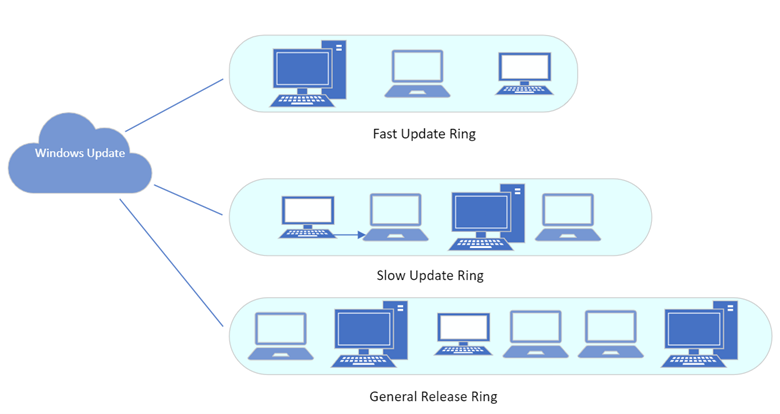
Windows Update for Business also gives you the ability to create update rings to fine tune the deployment of quality and feature updates. Rings specify how and when quality and Windows 10 and Windows 11 feature updates are applied. For instance, let’s say you want to deploy the Windows 11 feature update. For a large corporation you certainly wouldn’t want to install it on everyone’s computer at once right out of the gate. You would probably want your IT personnel group to receive the update first to allow them to test it out first. That would mean creating a fast update ring and assigning it to them. You would next want to update devices for power users such as software developers, graphical artists, etc. You would create a slower ring and, and so on. Below is an example of a 3-ring architecture.
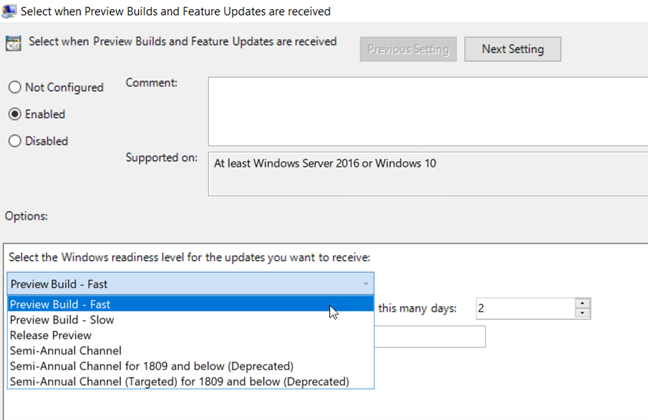
You can create these rings using the Group Policy Management Console. Create a GPO and go to Computer configuration > Administrative Templates > Windows Components > Windows Update > Windows Update for Business > Select “When Preview Builds and feature updates are Received.” Enable the policy and select the ring of your choice as is shown in the screenshot below. Then assign a deferral period for that ring. In the example below we have chosen a 2-day deferral period for the Fast Ring. We would then choose a longer period of perhaps 45-days for the slow ring.
To create rings for Quality Updates you would create a policy and go to Computer configuration > Administrative Templates > Windows Components > Windows Update > Windows Update for Business > Select when Quality Updates are Received.
Using MEM to Manage Windows Updates for Business
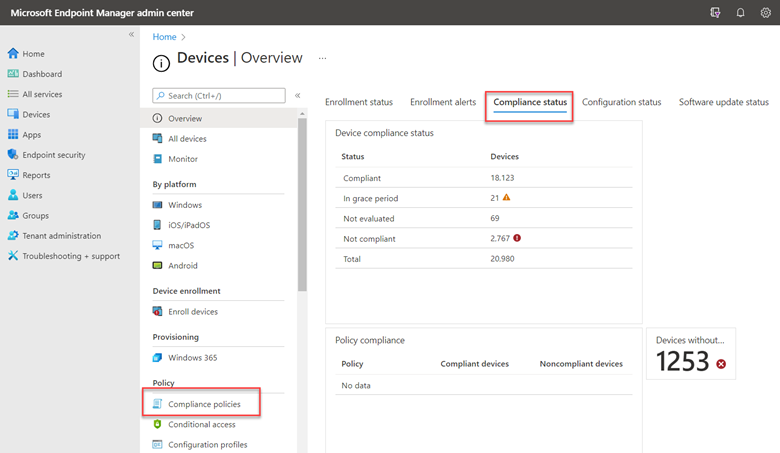
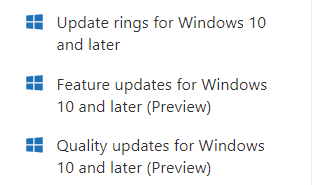
You can also use Microsoft Endpoint Manager to manage Windows Updates for Business. If you open MEM and go to Devices you will see 3 options.
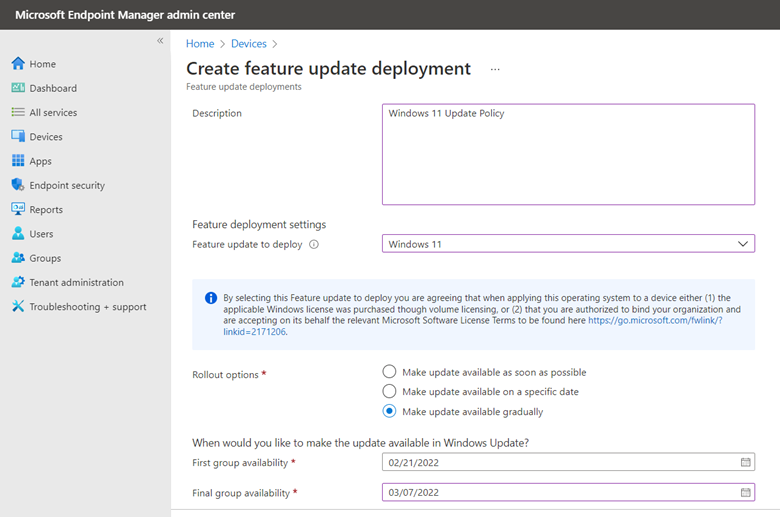
A small enterprise may not feel the need to utilize multiple update rings. If you want to simply deploy Windows 11 at large, click “Feature updates for Windows 10 and later” and select Windows 11 as the feature update. You can then choose between pushing the update as soon as possible, making it available on a specific date or gradually dispersing the update across your enterprise. In the example below I chose the third option and set a start and finish time for the deployment.
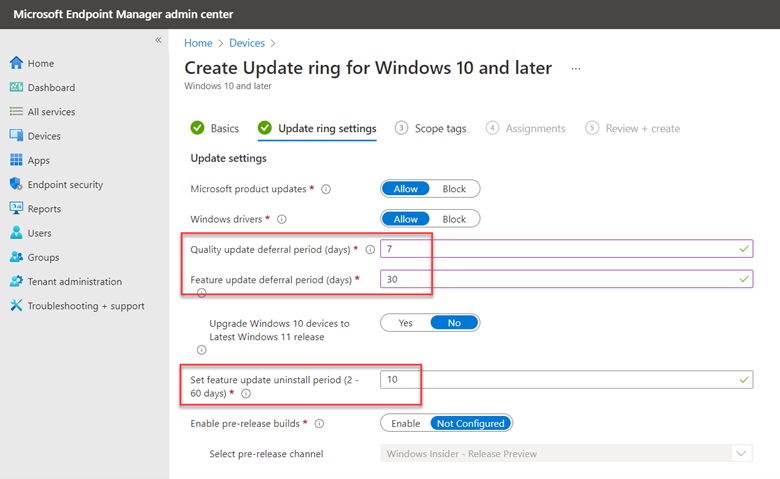
If you want to use update rings, the process is similar. Create a ring with your desired settings and assign it to a designated group. Note below the addition of an uninstall period that you can assign.
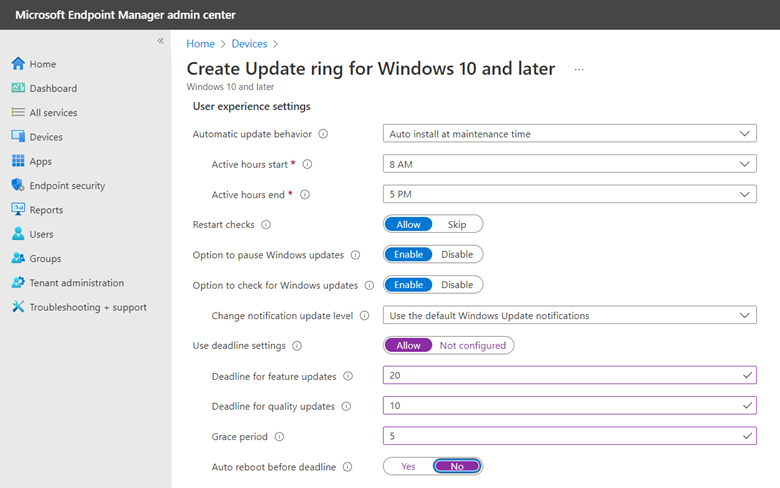
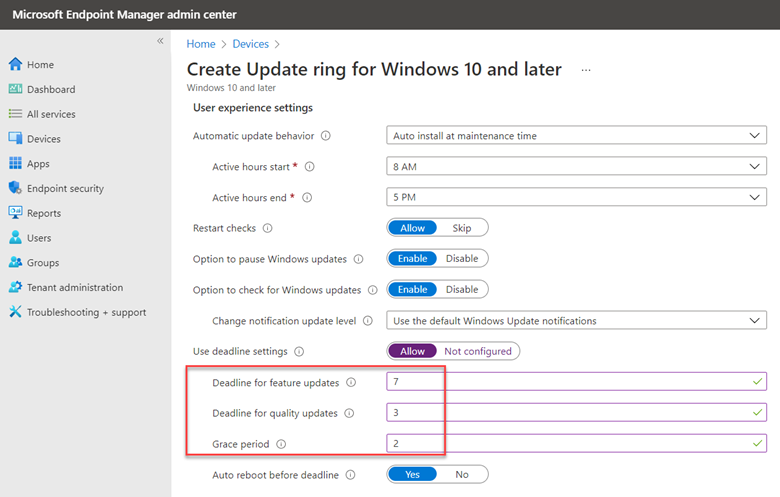
You can also configure User Experience settings for each ring. User experience settings give your users the ability to defer updates on their own when necessary. This would be important for a sales executive that is attending a sales conference for instance and needs the full use of their computer for an extended time. For instance, you can configure a grace period that specifies the number of days until a device is forced to restart. This would be useful for users returning to the office from extended leave or a long holiday period. You should first configure the active hours so that update-initiated reboots do not occur during this critical time window. You can then configure deadlines. In the screenshot below, users could defer feature updates on their own for 7 days, at which point the update would forcibly install.
Service Channels
Finally, there is something called Service Channels. Service channels define when features updates will be available. For instance, someone that is a member of the Windows Insider Program probably wants to receive feature updates in advance to preview them. Internal IT needs access to new feature updates ASAP to validate them for their desktop environments. These four channels are as follows:
- General Availability Channel – This is the default channel
- Windows Insider Dev
- Windows Insider Beta
- Windows Insider Release Preview
You can create policies using Group Policy or MDM to create policies that assign these channels.
Putting it all Together
Windows Update for Business obviously has a lot more moving parts than the media or WSUS methods. Things can get complex quickly. In part 3 of our ongoing series, we will look at an environment involving multiple Windows feature versions and deferral settings to see how the underlying processes occur to ensure that each device receives the updates it needs.